Last updated: November 14, 2024
OneLogin
An Identity Provider (IdP) vouches for the identity of a person through the use of an authentication token. Virtual Appliance uses IdP for several things, including logging in to the Admin Console and portals, deploying printers, releasing print jobs, and more.
If you use an IdP, the Control Panel Application (CPA) only supports badge and PIN authentication.
JIT Provisioning is the only option available when using OneLogin with the Virtual Appliance.
Configure Connection
To add and configure app properties for the Virtual Appliance connection do the following:
- Create OneLogin App.
- Add IdP Template.
- Configure Single Sign On.
- Configure Parameters.
- Add the X-509 Certificate.
- Complete IdP Settings.
- Assign Access.
- JIT Provisioning.
- Add Virtual Appliance Admins.
1. Create OneLogin App
- In your preferred browser log in to your OneLogin Admin Portal. https://<your domain>.onelogin.com/login
-
Hover your pointer over Applications in the top menu, then select Applications.
- Select Add App in the upper-right of the Applications window.
- Search for and select the SAML Custom Connector (Advanced) app.
- Give your app a unique display name and description.
- Select Save
Leave the current browser open to the new app page. To continue the app configuration, you need to open another browser and open the and access the service provider information.
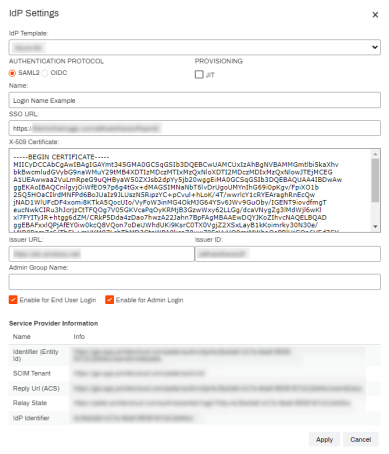
If the IdP Settings page does not look like the image shown below, you may not be using the latest version and should contact Product Support to upgrade your IdP settings.
2. Add IdP Template
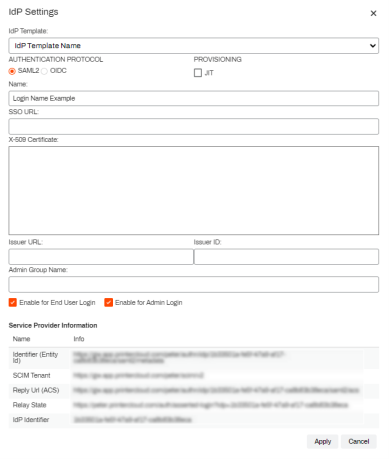
When configuring this IdP through Virtual Appliance, use the Custom option in the IdP Template drop-down.
- In a separate browser tab, open your Virtual Appliance Admin Console and sign in.
- Select Tools
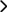 Settings
Settings  General, and scroll down to the Identity Provider Settings section.
General, and scroll down to the Identity Provider Settings section. - Select IdP, and then select Add.
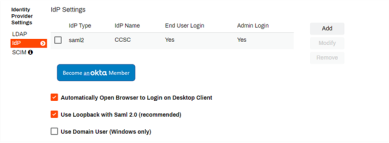
- Select the identity provider you want to configure in the IdP Template drop-down.
- Select SAML2 in the Authentication Protocol section.
-
For Provisioning it is assumed that JIT will be used for most Virtual Appliance applications. Check the box for JIT provisioning.
When you consider how to set up your IdP configuration be aware that SCIM provisioning requires an open connection from the IdP provider into the Virtual Appliance instance gateway container. We recommend JIT provisioning when setting up your IdP connection.
- In the Name field, enter the name you want displayed on the login button for users, e.g. My Company, Login, Acme Corp, etc.
- Scroll down and select the desired enable setting(s).
- Enable for End Users Login — Allows end users to login using this IdP. (Self-service Portal)
- Enable for Admin Login — Allows Admin users to login using this IdP. (Admin Console)
- Both boxes can be checked when using a single IdP, or if the admin and end users use the same IdP to log in.
Keep the IdP Settings screen open so that the Service Provider Information at the bottom is available for the following steps.
3. Configure Single Sign On
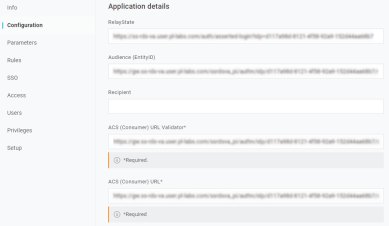
- In OneLogin, select the app's Configuration option from the left-side menu.
- In the Virtual Appliance Admin Console IdP Settings window, copy the Relay State and paste it into the OneLogin RelayState field.
- In the IdP Settings window, copy the Identifier (Entity ID) and paste it into the OneLogin Audience (Entity ID) field.
- In the IdP Settings window, copy the Reply URL (ACS) and paste it into both the OneLogin ACS (Consumer) URL Validator and ACS (Consumer) URL fields.
- Configure any other fields as desired, but they can be left with the default values.
- Select Save
- Select the OneLogin app's SSO option in the left-menu.
-
Copy the OneLogin Issuer URL and paste it into the Admin Console Issuer URL field.
Leave the Admin Console Issuer ID field blank.
- Copy the OneLogin SAML 2.0 Endpoint (HTTP) value and paste it into the Admin Console SSO URL field.
- Select Save
Configure Parameters
- Select the app's Parameters option in the left-menu.
-
Select the + button.
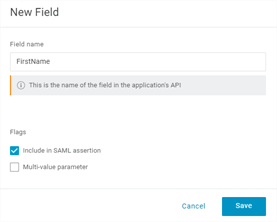
- In the Field name field enter “FirstName.”
-
Check the Include in SAML assertion box then select Save.
- In the Edit Field modal Value drop-down, select “First Name” then select Save.
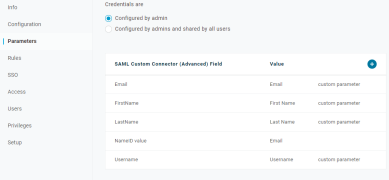
- Repeat these steps for the following parameters.
- Field Name: LastName, Value: Last Name.
- Field Name: Email, Value: Email.
- Field Name: Username, Value: Username.
- Select Save
4. Add the X-509 Certificate
- Select the OneLogin app's SSO option in the left-menu.
-
In the SSO window's X.509 Certificate section, right-click on the View Details link and select Open in new tab.
If you don't open the link in a new tab that's fine. After completing this section you'll need to navigate back to the app you created. Hover over Applications in the top-menu, select Applications, then select your app from the Applications page.
-
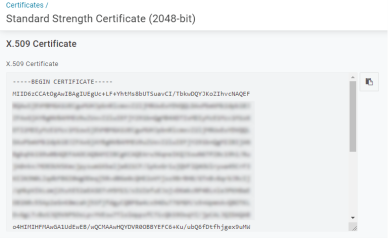
Scroll down to the X.509 Certificate section and copy the certificate body, including the Begin / End Certificate headers.
- Paste the certificate into the Admin Console X-509 Certificate field.
- Select Apply in Admin Console.
- Select Save at the top-right corner of the General page.
5. Complete IdP Settings
- On the Admin Console General page, navigate back to the Identity Provider Settings section.
-
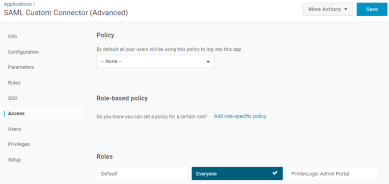
To have Virtual Appliance prompt your users to authenticate through the IdP when performing any function requiring authorization, such as installing a printer, select the Automatically Open Browser to Login on Desktop Client option.
If this option is not selected, the user must manually navigate to the IdP login screen to sign in.
-
We recommend enabling the Use Loopback with SAML2 option. The IdP needs to provide an authentication token to the desktop clients whenever authentication happens. This option allows the client to handle the token and automatically log in without interaction from end users.
- The option to Use Domain User (Windows only) will automatically authorize domain-joined Windows users and not require login via the configured IdPs.
- Select Save in the top-right corner of the General page.
6. Assign Access
- In the OneLogin Admin Portal, select the app's Access option.
- Select the Group(s) of users you want to have access to the Virtual Appliance application, and select Save.
- Select the Users option and verify the appropriate users have been assigned to the application.
7. JIT Provisioning
JIT does not support the provisioning of group membership associations, so you cannot apply RBAC roles, printer deployments or portal security roles to groups. All assignments have to be done individually for each user.
When using JIT Provisioning, the application creates users during the first sign-in attempt.
- Access your Virtual Appliance instance and select Sign in with <IdP Name>.
- Attempt to login with your IdP credentials.
-
This login attempt will fail and return you to the login page.
This is expected. With JIT, this action triggers the user creation in the instance.
- The following login attempt with valid credentials initiates a typical login sequence.
Administrators who need access to the Admin Console still need to be added to the Tools ![]() Users page using the steps in Admin Console Users.
Users page using the steps in Admin Console Users.
8. Add Virtual Appliance Admins
For steps on assigning users and roles to the Virtual Appliance Admin Console reference Admin Console Users.
-
New Mobile App Release
iOS: November 11th, 2024 -
Released: November 11th, 2024
-
Released: October 22nd, 2024
Updated Application Version Included